Teaclave Meetup #5
In Jun 24, we gathered in Zoom for the fifth monthly Teaclave meetup. In this meetup, we're glad to have Hongbo (@ya0guang) talking about his contributions on adding WebAssembly Micro Runtime to Teaclave as an executor (PR: #504, #512).
Schedule
- Recent update of Teaclave, Mingshen (5m)
- Executing WebAssembly in Teaclve, Hongbo (40m)
- Open discussion
Notes
Recent Update of Teaclave
Teaclave TrustZone SDK version 0.1.0 released
- Vote result: https://lists.apache.org/thread.html/r441addf283f6c8780326f372e39a9d723164f6d910184ea3686a5c4a%40%3Cdev.teaclave.apache.org%3E
- Release notes: https://github.com/apache/incubator-teaclave-trustzone-sdk/releases/tag/v0.1.0
- Download link: https://teaclave.apache.org/download/
Linaro OP-TEE Contributions meeting
- Recording: https://linaro-org.zoom.us/rec/share/0o3Ku4zaXSrP-Ep0WI5P-XB-KAiP5d94kXbKmg43VqrnRHUmsLV_sv1wI01JbL0C.kSM-ov2pc9Sggf, Passcode: 9c.&%KR6
- Slides: https://drive.google.com/file/d/1YPig8k-xRyeRxuu1ALTmkqY-nxtH5upR/view?usp=sharing
Executing WebAssembly in Teaclave

Some question and discussion:
- Can we reuse the WebAssembly runtime to improve the performance of startup?
- Bridging
tlibcfunctions into WAMR.
Open Discussion
- ARM CCA: https://www.arm.com/why-arm/architecture/security-features/arm-confidential-compute-architecture
- EdgelessSys mablerun: https://github.com/edgelesssys/marblerun
- Attestation mechanism in Google Cloud Confidential Computing
Announcing Apache Teaclave™ TrustZone SDK (incubating) 0.1.0
On behalf of the Teaclave community, I am happy to announce the release of Teaclave TrustZone SDK 0.1.0. This is the first Apache Incubator release since the recent donation to the Teaclave community.
Teaclave TrustZone SDK provides abilities to build safe TrustZone applications in Rust. The SDK is based on the OP-TEE project which follows GlobalPlatform TEE specifications and provides ergonomic APIs. In addition, it enables capability to write TrustZone applications with Rust's standard library and many third-party libraries (i.e., crates). Teaclave TrustZone SDK is a sub-project of Apache Teaclave™ (incubating). To learn more about the design and history of TrustZone SDK, please read the blog Welcome Rust OP-TEE TrustZone SDK To Teaclave.
Highlights
This version implements the following Rust APIs in GlobalPlatform TEE specifications:
TEE Client API (optee-teec)
- Context
- Error
- Operation
- Parameter
- Session
- UUID
TEE Internal Core API (optee-utee)
- Arithmetical
- Crypto Operation
- Error
- Object
- Parameter
- Time
- Trace
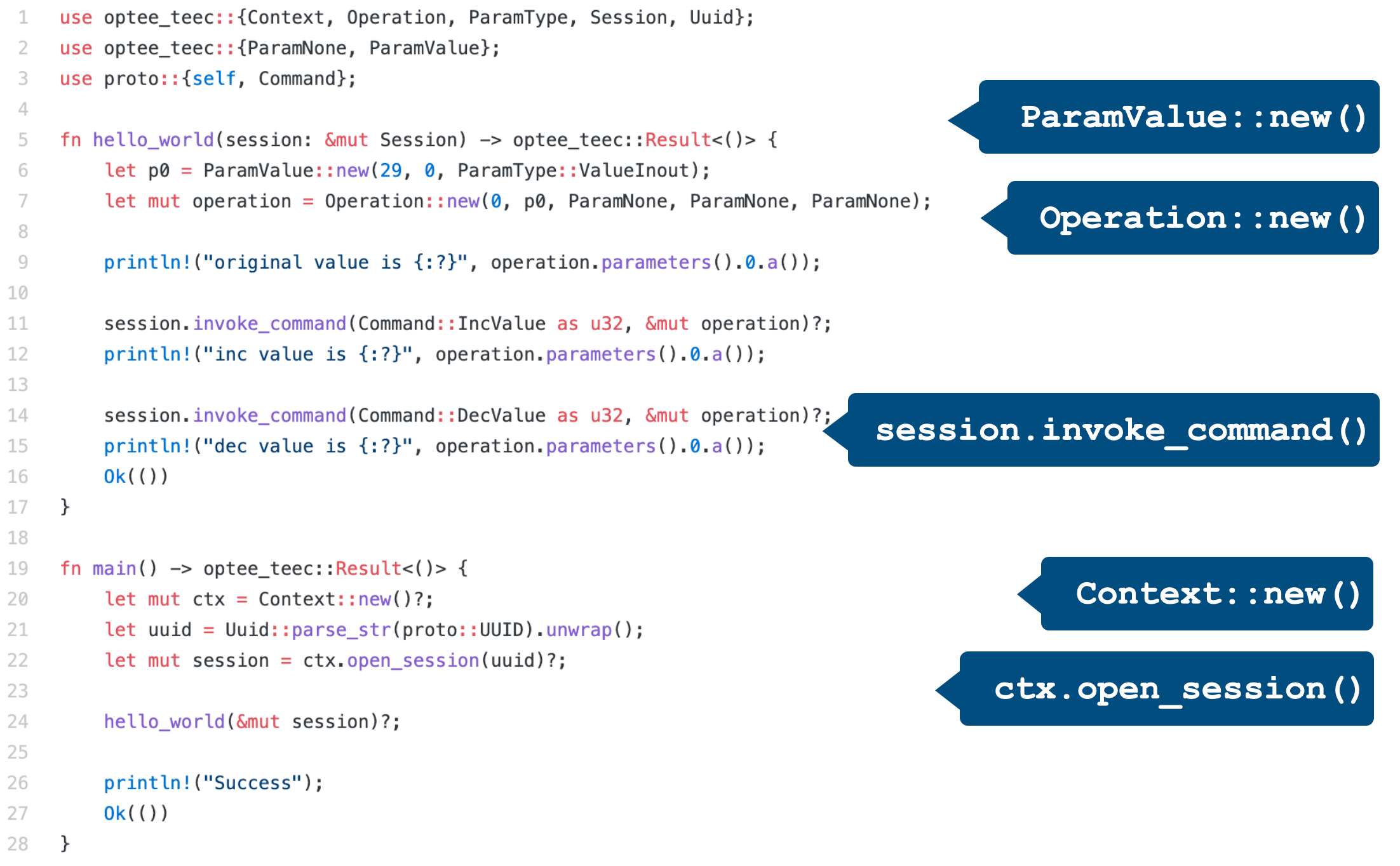
Here is a demonstration of using these Rust APIs to open a session and invoke a function to TA.
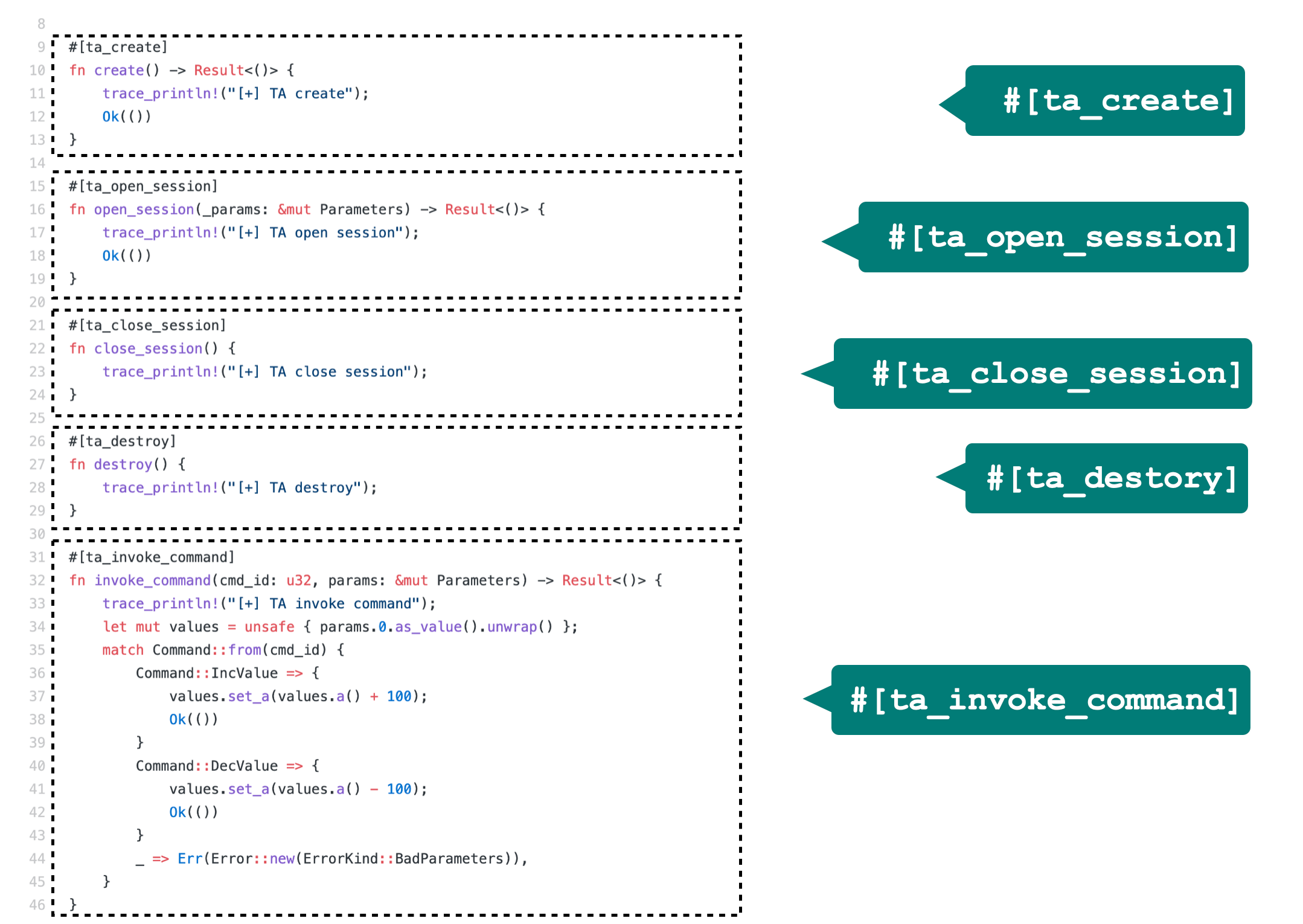
We also provides procedure macros to automatically generate bindings interfaces of TA:
#[ta_create],#[ta_destroy],#[ta_open_session],#[ta_close_session],#[ta_invoke_command]
These annotations will automatically generate helper functions to bridge the normal/secure worlds.
This version includes rewrites of all examples (e.g., AES, authentication, big
integer, HOTP) from OP-TEE repository. In addition, we include more examples
using serde for serialization and deserialization.
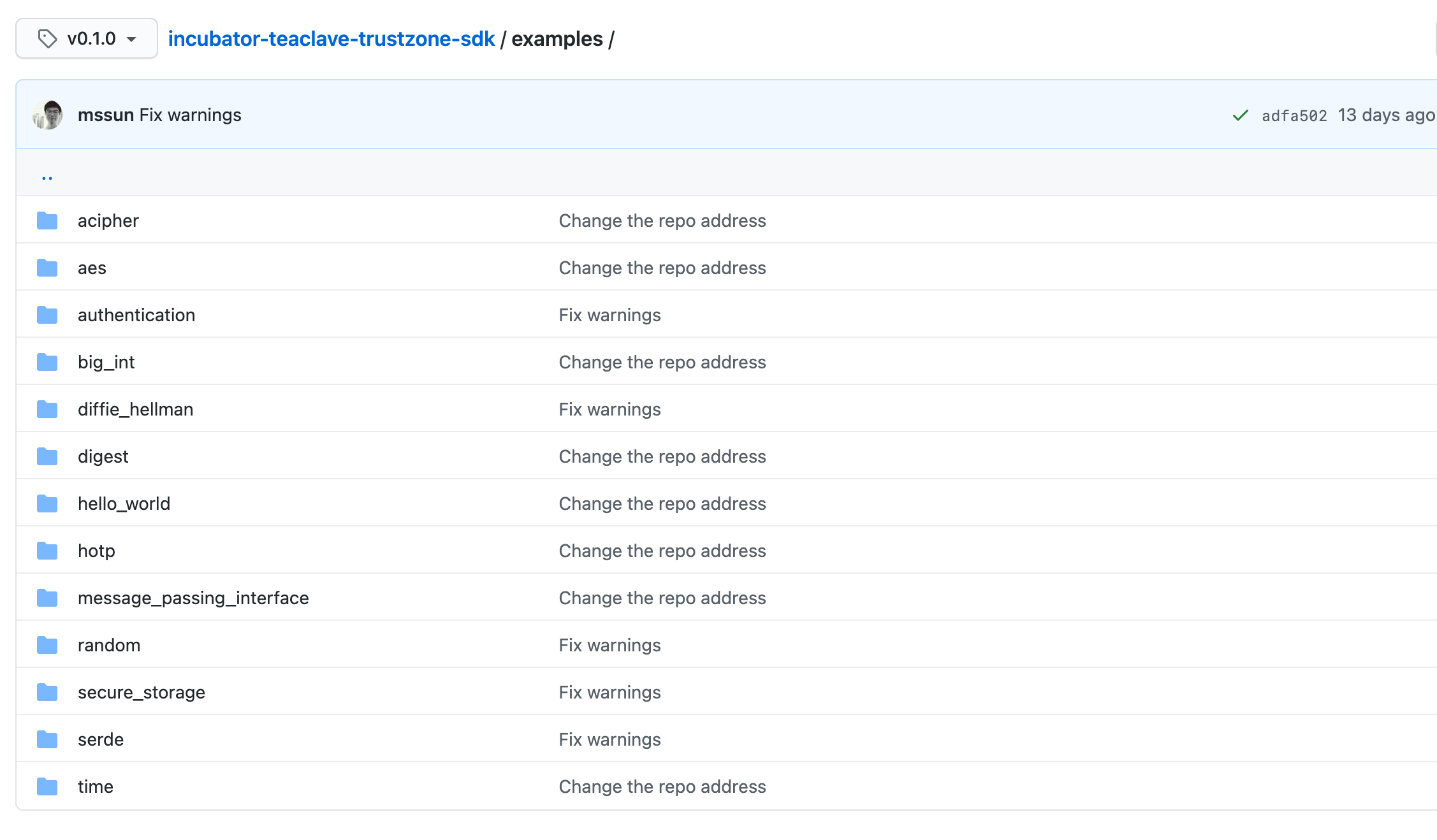
This version is compatible with OP-TEE 3.13.0.
Getting Started
Here is a simple instruction to download, build and test the TrustZone SDK:
$ wget https://dist.apache.org/repos/dist/dev/incubator/teaclave/trustzone-sdk-0.1.0-rc.1/apache-teaclave-trustzone-sdk-0.1.0-rc.1-incubating.tar.gz
$ tar zxvf apache-teaclave-trustzone-sdk-0.1.0-rc.1-incubating.tar.gz && cd
apache-teaclave-trustzone-sdk-0.1.0-incubating
$ # Instructions to verify the source tar:
https://teaclave.apache.org/download/#verify-the-integrity-of-the-files
$ # Building
$ docker run --rm -it -v$(pwd):/teaclave-trustzone-sdk -w
/teaclave-trustzone-sdk teaclave/teaclave-trustzone-sdk-build:0.1.1
bash -c "source environment && make"
$ # Testing
$ docker run --rm -it -v$(pwd):/teaclave-trustzone-sdk -w
/teaclave-trustzone-sdk teaclave/teaclave-trustzone-sdk-build:0.1.1
bash -c "source environment && cd ci && ./ci.sh"
We also provide a document Getting Started with OP-TEE for QEMU ARMv8 to get started step by step.
Download
You can download the release from the download page. Also, please checkout our repository hosted on GitHub.
Contributing
Teaclave TrustZone SDK is under the Apache License v2 and open source in The Apache Way. We aim to create a project that is maintained and owned by the community. All kinds of contributions are welcome. Thanks to our contributors.
Accepting Rust OP-TEE TrustZone SDK to Apache Teaclave™ (incubating) Proposal
Abstract
Rust OP-TEE TrustZone SDK provides abilities to build safe TrustZone applications in Rust. The SDK is based on the OP-TEE project which follows GlobalPlatform TEE specifications and provides ergonomic APIs. More information can be found at the project repository: https://github.com/sccommunity/rust-optee-trustzone-sdk.
Proposal
Rust OP-TEE TrustZone SDK provides abilities to build safe TrustZone applications in Rust.
Background
The Rust OP-TEE TrustZone project is being actively developed within Baidu. It was open source on Jan 30, 2019.
Rationale
ARM TrustZone is another hardware trusted execution environment implementation. The goal of Teaclave is to provide a universal secure computing platform which is agnostic with TEE implementation. Currently, Teaclave has Teaclave SGX SDK and only supports Intel SGX. With the Rust OP-TEE TrustZone SDK, we can build the Teaclave platform on ARM TrustZone.
Initial Goals
- Transfer repository to the Apache Incubator under the Teaclave project
- Code cleanup and more documentation
Meritocracy:
The Rust OP-TEE TrustZone SDK project was originally developed by Shengye Wan and Mingshen Sun within Baidu. The project now has new committers from around the world. Some open source projects like https://github.com/veracruz-project are using the SDK to build their systems. We encourage everyone to ask questions and create pull requests to the project.
Community:
We see several open source projects which are using the SDK for development. Also, we already receive contributions from external comitters. The community is growing overtime.
Core Developers:
The core developers are:
- Shengye Wan (simonsywan at gmail dot com)
- Mingshen Sun (mssun at apache.org)
Alignment:
The project is a complimentary of Teaclave's TEE backends.
Known Risks
An exercise in self-knowledge. Risks don't mean that a project is unacceptable. If they are recognized and noted, then they can be addressed during incubation.
Project Name
Since the project will be accepted as a subproject in Teaclave, the project is renamed to Teaclave TrustZone SDK.
Inexperience with Open Source:
One of the core developers, Mingshen Sun is from the Teaclave community. He's familiar with The Apache Way for the open source community.
Length of Incubation:
The project will be in incubation with Apache Teaclave™ (incubating) project.
Documentation
Initial Source
Source and Intellectual Property Submission Plan
We will submit a Software Grant for this project later.
External Dependencies:
The dependencies have Apache compatible license, which is provided under the BSD 2-Clause license.
Cryptography:
N/A
Required Resources
Mailing lists:
The project shares the same mailing list of Teaclave.
Git Repositories:
- https://gitbox.apache.org/repos/asf/incubator-teaclave-trustzone-sdk.git
- https://github.com/apache/incubator-teaclave-trustzone-sdk
Issue Tracking:
Same with Teaclave.
Other Resources:
N/A
Initial Committers
- Mingshen Sun (mssun at apache dot org)
- Shengye Wan (simonsywan at gmail dot com)
Teaclave Meetup #4
In April 29, we gathered in Zoom for the third monthly Teaclave meetup. In this meetup, we're glad to have Jiang Jun from Phala Network to give a talk on Taclave SGX SDK meets Substrate. Phala Network is a decentralized confidential computing cloud with tech stack includes Teaclave SGX SDK and Substrate.

In the meetup, we discuss use cases, technical details and implementation of Phala Network, as well as some difficulties with current version of Teaclave SGX SDK.
We are continuing work with out community together to improve the projects. Hopefully, more users and developers can join in our community and share your experience.
At last, if you are interested in our meetup, please subscribe our mailing list for the latest schedule of meetups.
Teaclave Meetup #3
In March 25, we gathered in Zoom for the third monthly Teaclave meetup. In this meetup, we're glad to have two speakers talking about some initial progress of Teaclave verification and comparison of public cloud attestation services.
Schedule
- Recent Update of Teaclave, Mingshen (3m)
- Teaclave Verification, Sean (15m)
- Comparison of Public Cloud Attestation Services, Mengyuan Li (45 m)
Teaclave Verification
In this session, Sean talked introduced the plan of Teaclave verification. The main ideas is to create formal descriptions, specifications, and proofs for some core components of Teaclave.
The initial effort on this field is trying to formally describe the access control module in Teaclave. And then prove it with requirements defined in Common Criteria for Information Technology Security Evaluation. The security objective of access control module is to prevent unauthorized users from accessing the critical data through tasks and functions. By achieving the security objective, the threats of runtime tasks and functions abuse are eliminated under the assumptions identified in security problem definition. With these objectives, we can find some corresponding requirements in Common Criteria, e.g., FIA_UAU.2 for user authentication before any action.
The initial work has been accepted as a separate project in Teaclave. If you are interested in this topic, please see https://github.com/apache/incubator-teaclave-verification to learn more.
Comparison of Public Cloud Attestation Services
Then, Mengyuan talked his recent research on attestation, especially, on public cloud attestation services.

Here the abstract of the talk:
Confidential computing is an emerging security feature provided by more and more public cloud service providers (e.g., Amazon AWS, Microsoft Azure, and Google Cloud) in order to help customers protect their sensitive data in the cloud environment. Some popular confidential computing services include Intel Software Guard Extensions (SGX) enclaves and AMD Secure Encrypted Virtualization (SEV) VMs. These services are usually atop different hardware-based Trusted Execution Environments (TEE) technologies.
Meanwhile, to help convince the customers the trustworthiness of the platform hardware and the integrity of codes inside the TEE, cloud services providers also offer remote attestation services. In this talk, we will first cover the remote attestation workflow provided by some famous cloud TEE services, including Azure Open Enclave, Nitro Enclave, Google confidential computing VM and Fortanix. From the perspective of customers, we also focus on the attestation reports the customers can get. We then introduce Teaclave's current attestation design and discuss the attestation report standard Teaclave should follow.
He also discussed the attestation design of Teaclave.
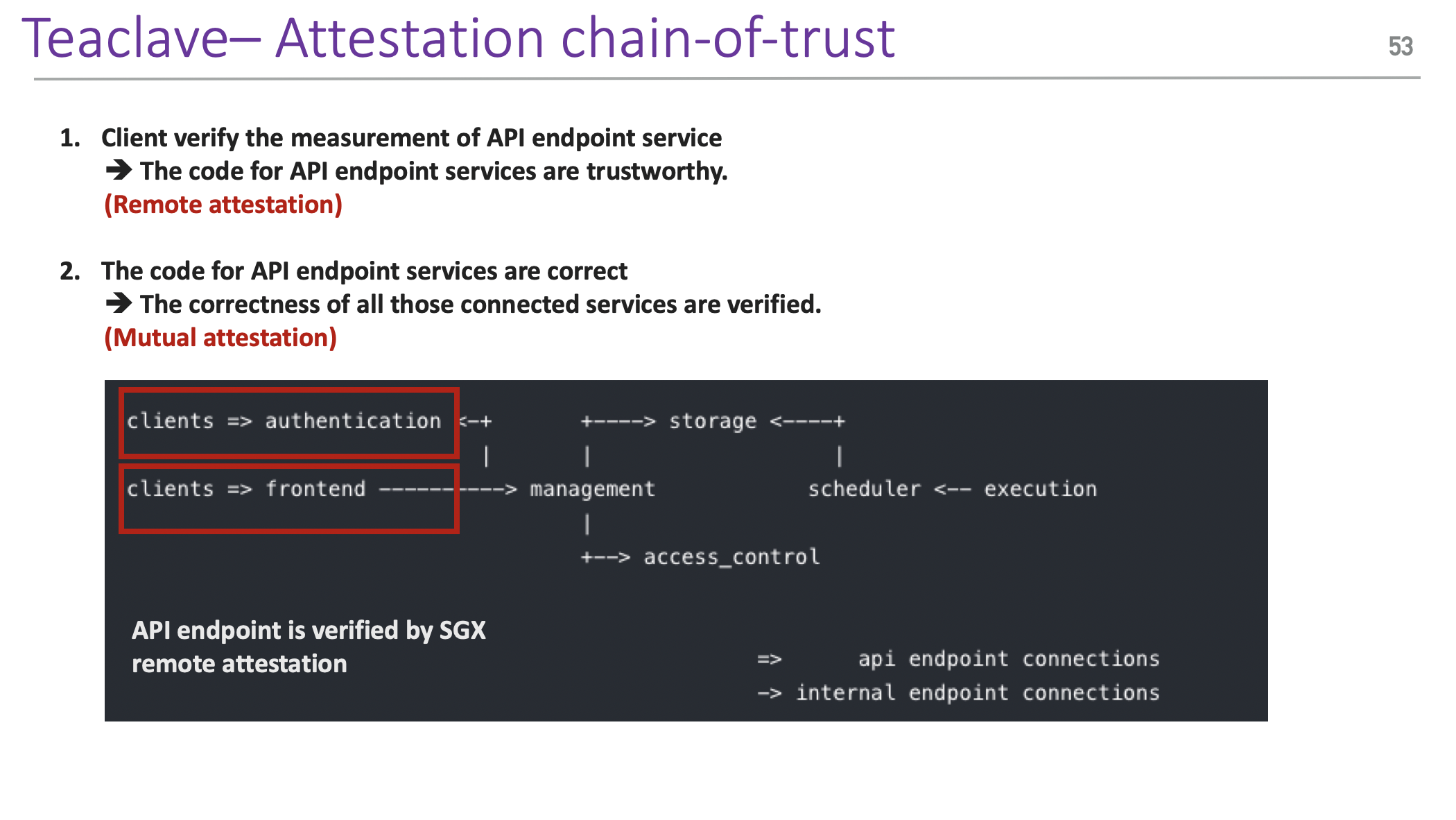
In the end, he also summarized the roles in the attestation ecosystem and positions of services/products discussed in this talk.

At last, thanks for attending this meetup. I'll continue to drive this meetup and make it a monthly activity for the community. If you want to speak in the next time, please post your proposed topic in the mailing list. I'll help you to schedule the time.
欢迎 Rust OP-TEE TrustZone SDK 成为 Teaclave 子项目
TrustZone 为手机、嵌入式设备、云计算等 ARM 生态提供安全的可信执行环境,用于包括 安全支付、密钥管理、模型保护等场景。但是由于内存安全问题,TrustZone 中运行的安全 应用 (trusted application 或叫 TA) 的安全性大打折扣。 例如高通 QSEE 内存安全问题 [1] 造成的安全世界(secure world) 的漏洞, 后果甚至可以拿到全磁盘加密的密钥 [2]。
2019 年初百度开源了 Rust OP-TEE TrustZone SDK,为当今广泛使用的开源 TrustZone 实 现 OP-TEE 提供了一套内存安全、使用方便的 SDK。SDK 基于 GlobalPlatform 的 TEE 标准,为开发者提供标准的开发接口。除此之外 Rust OP-TEE TrustZone SDK 支持 标准库和第三方库,提高了 TA 的开发速度,并扩展了 TrustZone 的应用场景。
为了加速隐私安全生态发展,完善 TrustZone 的技术基础设施,百度在 2021 年初正式把 项目捐赠给 Apache 基金会,作为 Teaclave 的子项目之一,同时更名为 Teaclave TrustZone SDK,新的项目代码库地址为: https://github.com/apache/incubator-teaclave-trustzone-sdk 。Teaclave TrustZone SDK 与 Teaclave SGX SDK 一样,可以为 Teaclave FaaS 隐私安全 计算平台提供底层支持,赋能多平台可信执行环境的隐私安全计算生态。
Teaclave TrustZone SDK 设计和实现
Teaclave TrustZone SDK 在 GlobalPlatform 标准的 API 上重新设计了安全的 Rust 接口, 使用 Rust 编写 TA(图中的 trusted apps)和 app(图中 client apps)能够大大减少内 存安全问题,确保可信执行环境的安全。
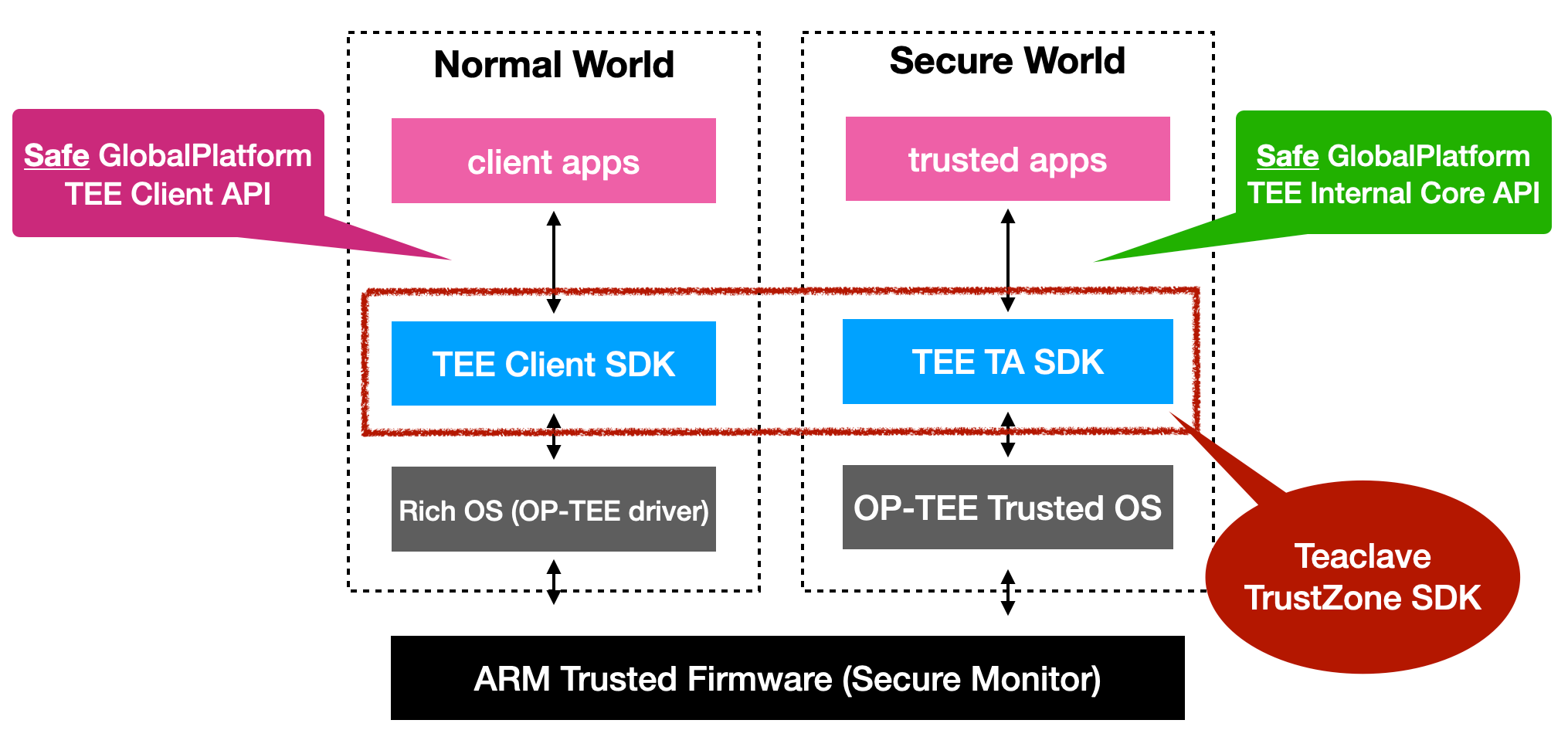
通过使用 Rust 的过程宏(procedure macro)自动生成边界代码,减少了开发中不必要的
负担,并且能够避免开发中因为粗心造成的安全问题。如下图所示,只需要在相应的函数上
加 #[ta_create], #[ta_open_session], #[ta_close_session], #[ta_destory],
#[ta_invoke_command]。

通过利用 Rust 的丰富的类型系统,能在编译时报告内存安全问题,例如下图中对于 client 的实现,相比复杂并且类型简单的 C 接口,Rust API 语义更清晰,并提供强类型 检查。

项目中提供了 13 个样例程序,包括加解密,安全存储,HOTP 等等。同时,我们还展示了 使用 Rust 的第三方库 serde 作为边界的序列化来传递复杂参数,避免出现安全边界设计 不当引发的内存安全问题。
快速上手、文档
Teaclave TrustZone SDK 的 API 都提供了对应的文档,在项目 Wiki 中,我们提供了一个 快速上手的例子,在 QEMU 模拟器中运行使用 TrustZone SDK 的 trusted app。链接如下: https://github.com/apache/incubator-teaclave-trustzone-sdk/wiki/Getting-started-with-OPTEE-for-QEMU-ARMv8 。更多关于 Teaclave TrustZone SDK 的设计和性能等都在论文 RusTEE: Developing Memory-Safe ARM TrustZone Applications 中找到,此论文也收录于 ACSAC 2020。
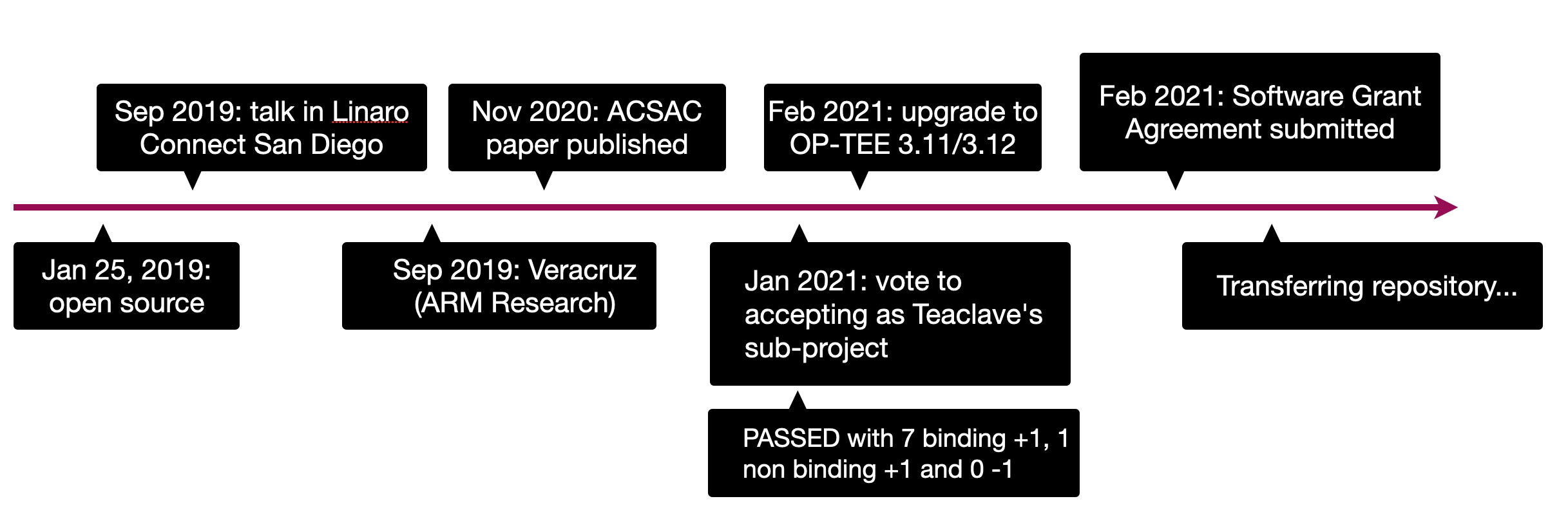
Teaclave TrustZone SDK 时间线
- 2019 年初开源。
- 2019 年在 Linaro Connect 和 RustCon Asia 对外发布,得到了 ARM 的支持,现在其隐私计算相关项目中使用。
- 2020 年相关文章发表在国际顶级安全会议 ACSAC,得到学术界肯定。
- 随着隐私安全计算的发展,多个开源项目开始使用,例如由 ARM Research 主导的 Veracruz 开源项目使用 SDK 构建其隐私计算试验项目,Veracurz 也将加入隐私计算联盟(Confidential Computing Consortium)。
- 2021 年 2 月升级 TrustZone SDK 支持 OP-TEE 3.11 和 3.12。
- 2021 年 2 月启动项目捐赠流程,通过社区投票并提交 Software Grant Agreement。
- 2021 年 3 月项目 repository 正式移交到 Apache 组织下,隶属于 Apache Teaclave™ (incubating) 项目。
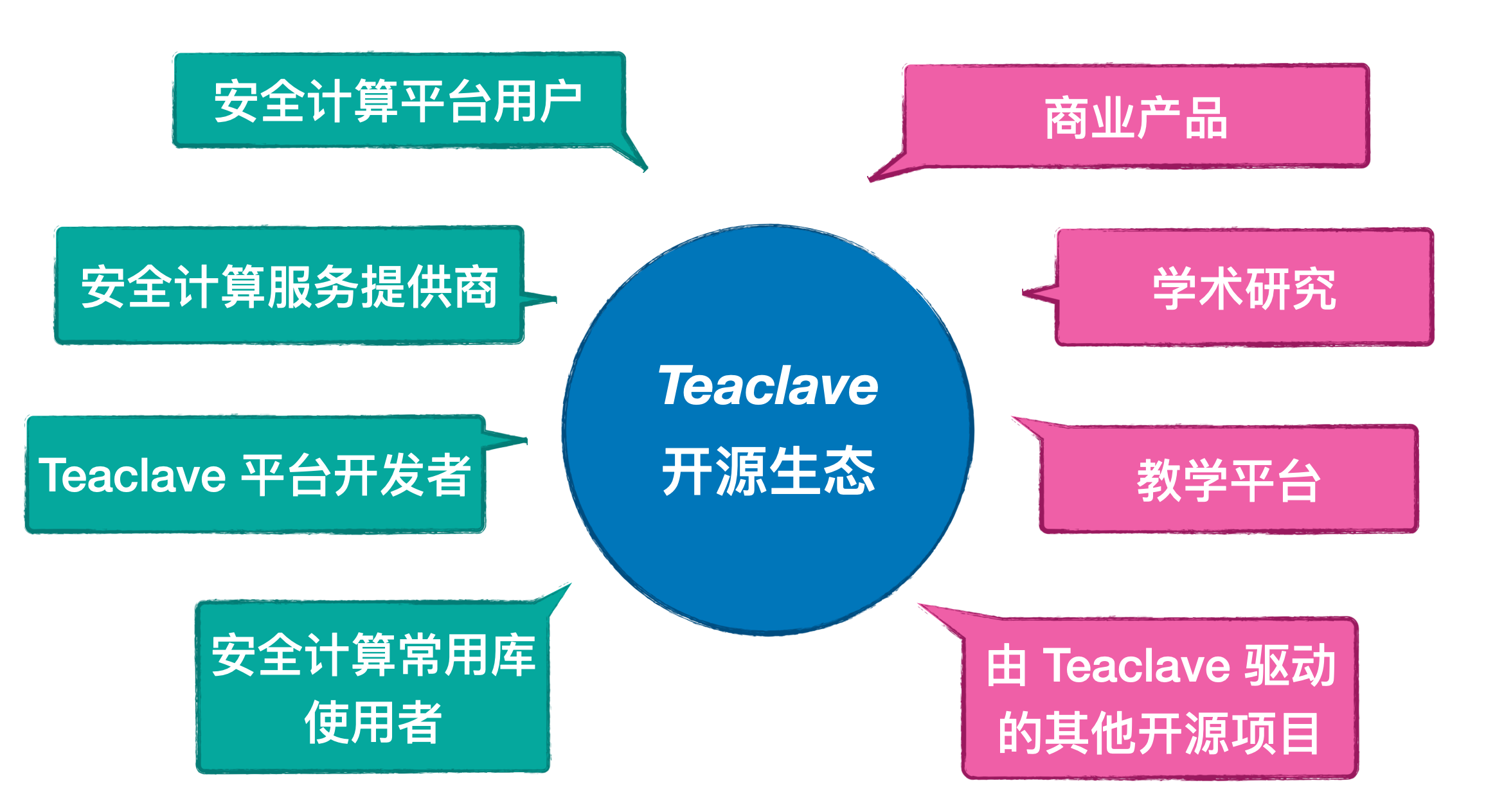
Teaclave 开源社区
TrustZone SDK 加入 Apache 后,将与 Teaclave 开源社区共同发展,非常欢迎大家的贡献, 一起推动隐私安全计算生态 。已有至少四家公司或组织在产品中使用 Teaclave,并且有超 过九个开源项目使用了 Teaclave 平台和 Teaclave SGX SDK。这些都给项目的发展提供源 源不断的动力。更多信息可以在我们的官网 community 下查看: https://teaclave.apache.org/community/
Teaclave 的开源是 The Apache Way (https://www.apache.org/theapacheway/) 的开源,无论是代码、文档、设计还是路线图规划,我们都会在社区的各个渠道中讨论。如 果 你想关注 Teaclave,亦或想加入我们的讨论,可以在 Github issues,邮件列 表 回复我们、发起新的话题。也可以关注我们的 Twitter 账号 @ApacheTeaclave了解最新动态。除此之外, 我们在官网 (https://teaclave.apache.org/)中提供了 Teaclave 相关的演讲、论文和文章,包括 TrustZone SDK 之前的演讲 slides 以及视频。
参考链接:
[1] Qualcomm's Secure Execution Environment (QSEE) privilege escalation vulnerability and exploit (CVE-2015-6639) : http://bits-please.blogspot.com/2016/05/qsee-privilege-escalation-vulnerability.html
[2] Extracting Qualcomm's KeyMaster Keys - Breaking Android Full Disk Encryption: http://bits-please.blogspot.com/2016/06/extracting-qualcomms-keymaster-keys.html
Welcome Rust OP-TEE TrustZone SDK to Teaclave
TrustZone is a security feature by ARM SoC to provide a trusted execution environment to protect areas like mobile computing, edge computing, and emerging confidential computing, supporting scenarios like payments, key management, model protection, etc. However, one major security threat in TrustZone applications is the memory safety issue. For instance, a vulnerability of Qualcomm's QSEE is caused by the memory safety issue [1]. Attackers can even get the full-disk encryption key by exploiting such kind of vulnerability [2].
In 2019, Baidu open sourced the Rust OP-TEE TrustZone SDK project, enabling safe, functional, and ergonomic development of TrustZone app developments. The SDK provides a safer APIs based on the GlobalPlatform's TEE standard. In addition, Rust OP-TEE TrustZone SDK also support Rust's standard library and third-party crates (i.e., libraries). This will improve the efficiency of developments of TrustZone apps, and also extend its usage scenarios.
To accelerate the development of confidential computing ecosystem and improve TrustZone's foundation, Baidu has donated Rust OP-TEE TrustZone SDK to Apache Software Foundation as a subproject of Teaclave, and renamed it as Teaclave TrustZone SDK. The location of new repository is https://github.com/apache/incubator-teaclave-trustzone-sdk. Similar to Teaclave SGX SDK, Teaclave TrustZone SDK will be the foundation of Teaclave FaaS platform to support multiple trusted execution environments.
Design and Implementation of Teaclave TrustZone SDK
Based on the GlobalPlatform's C APIs, Teaclave TrustZone SDK provides safer Rust interfaces. With the SDK, TrustZone apps will not be affected by any memory safety issues caused by the Rust's strong type system.

We also created procedure macros to help developments. For example, developers
can simply put
#[ta_create], #[ta_open_session], #[ta_close_session], #[ta_destory],
and #[ta_invoke_command] annotations before corresponding functions. These
annotations will automatically generate helper functions to bridge the normal/secure worlds.

By using the rich type system of Rust, the memory safety issues will be reported at compile time. For example, in the following case, compared to C's APIs, the Rust APIs have clearer semantics and more strict type checking.

The project also has 13 samples, including encryption/decryption, secure storage, HOTP, etc.
Also, we provide a message passing sample code by using serde for
serialization and de-serialization between different worlds to avoid any
security issues caused by improper design in boundaries.
Getting Started and Documentations
All APIs in Teaclave TrustZone SDK are well documented. In the project's Wiki page, we have a quick-start document to guide you compiling and running a TrustZone app in QEMU emulators. You can find more design and performance evaluation in our paper published in ACSAC 2020.

Teaclave TrustZone SDK Timeline
- 2019: Open source.
- 2019: Talks in Linaro Connect and RustCon Asia.
- 2020: Technical report published in ACSAC 2020.
- 2020: Many open source projects started to use the SDK. E.g., Veracruz by ARM Research is an experimental projects on confidential computing using the SDK.
- Feb 2021: Support OP-TEE 3.11 and 3.12.
- Feb 2021: Initial the donation procedure.
- Mar 2021: Officially transferred to Teaclave.

References:
[1] Qualcomm's Secure Execution Environment (QSEE) privilege escalation vulnerability and exploit (CVE-2015-6639) : http://bits-please.blogspot.com/2016/05/qsee-privilege-escalation-vulnerability.html
[2] Extracting Qualcomm's KeyMaster Keys - Breaking Android Full Disk Encryption: http://bits-please.blogspot.com/2016/06/extracting-qualcomms-keymaster-keys.html
Apache Teaclave™ (incubating) 0.2.0 发布
Apache Teaclave™ (incubating) 是一个隐私安全计算平台,为隐私数据计算赋能。基于硬 件安全能力,Teaclave 确保敏感数据在可信域外和离岸场景下安全可控的流通和处理,无 需担心隐私数据泄露和滥用。 Teaclave 同时支持多方参与的联合计算,打破企业和组织中 的数据孤岛。Teaclave 于 2019 年由百度捐赠进入 Apache 基金会孵化器。在 2020 年 10 月发布第一个开源社区版本。
Teaclave 使用 Intel SGX, 提供基于硬件隔离、内存加密、远程证实等安全技术保护数据 隐私计算任务。 Teaclave 平台提供了函数即服务(function-as-a-service)接口,降低 了使用门槛。平台中也实现了众多内置函数,例如机器学习算法,多方联 合求交,加解密 计算等等常用功能。更重要的是,开发者还可以使用 Python 自由编写函数来操作隐私数据, 在中平台执行。最后,为了避免内存安全漏洞带来的安全风险,Teaclave 还使用内存安全 编程语言 Rust 编写。
2021 年 3 月 2 日,我们迎来了 Teaclave 第二个社区版本的发布 0.2.0。在这一版本中, 我们重点放在提供更多的内建函数,不同语言的客户端 SDK,更方便的 docker 部署环境, 命令行接口,文档等等。
Teaclave 0.2.0 亮点介绍
在 0.2.0 中,我们添加了多种语言的客户端 SDK,现在我们提供了 Python、Rust、C、 Swift 四种语言的接口,在 Teaclave Meetup #2 中,我们已经介绍了不同语言 SDK 的组 织结构和框架。简单来说,我们使用 JSON 序列化/反序列化的方式作为多语言的边界。下 图描述了这几种语言 SDK 的关系,以及一些事例的接口。
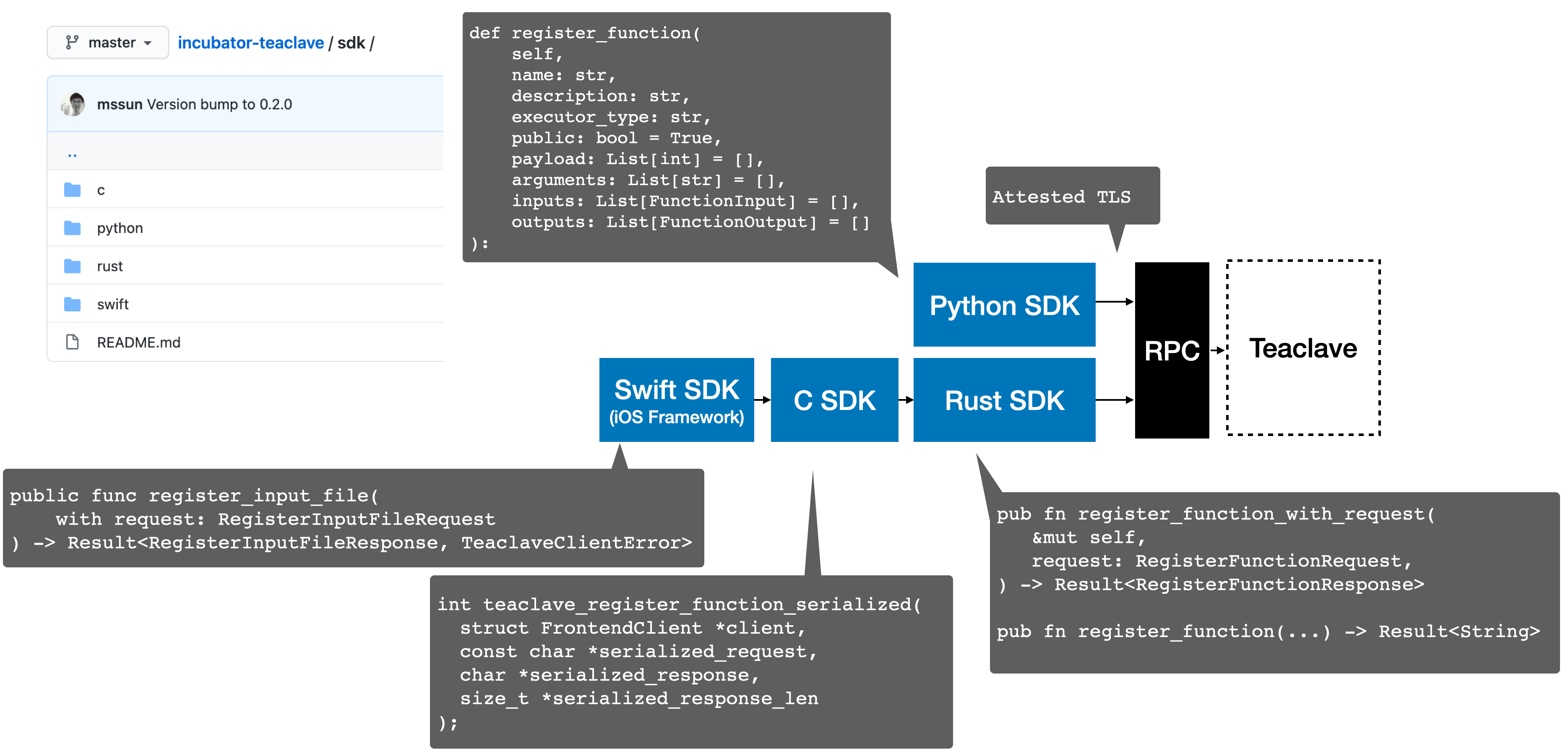
Teaclave 0.2.0 版本详情
详细来讲 0.2.0 包括一下修改以及新功能:
Functions
- 增加内置的 PCA (Principal Component Analysis) 函数
- 添加泄漏密码查询内置函数 (#447)
SDK
- 增加 Rust 客户端 SDK (#455)
- 增加 C 客户端 SDK (#470)
- 增加 Swift 客户端 SDK,也就是 iOS framework
- 修改 SDK 中接口的 CMAC 格式为 byte array
Docker
- 增加
teaclave-file-service容器作为示例程序的远程文件系统 (#446) - 修复在仿真模式下的 docker compose 文件 (#462)
CLI
- 增加
attesation的子命令,可以展示当前 SGX 平台的远程认证报告
文档
- 增加 codebase 中的文档
- 增加在 Azure Confidential Compute VM 中部署 Teaclave 的文档介绍
其他
- 在 binder 模块中增加 input/output buffer 的检查以及测试
- 使用 Github Action 进行 PR 的编译、测试以及格式检查
- 文档的打磨
如何下载
Teaclave 0.2.0 版本可以在官网下载页面找到(注意验证 PGP 签名和 hash)。
快速入门
如果您想尝试使用 Teaclave,我们提供了一个简单的上手文档(https://teaclave.apache.org/docs/my-first-function/)来执行一个打印 hello world 的函数。
简单来说,你可以通过以下命令使用 docker 编译 Teaclave:
$ cd incubator-teaclave
$ docker run --rm -v $(pwd):/teaclave -w /teaclave \
-it teaclave/teaclave-build-ubuntu-1804-sgx-2.9.1:latest \
bash -c ". /root/.cargo/env && \
. /opt/sgxsdk/environment && \
mkdir -p build && cd build && \
cmake -DTEST_MODE=ON .. && \
make"
然后使用 docker-compose 在仿真模式下执行 Teaclave 的所有服务:
$ (cd docker && docker-compose -f docker-compose-ubuntu-1804-sgx-sim-mode.yml up --build)
最后,就可以在 examples 目录下使用 Python 调用 echo 函数打印 "Hello, Teaclave!":
$ cd examples/python
$ PYTHONPATH=../../sdk/python python3 builtin_echo.py 'Hello, Teaclave!'
[+] registering user
[+] login
[+] registering function
[+] creating task
[+] approving task
[+] invoking task
[+] getting result
[+] done
[+] function return: b'Hello, Teaclave!'
如果你想深入的了解 Teaclave 的内部设计和实现,我们还有更多设计文档、API 文档、代码库文档等你发现。
Announcing Apache Teaclave™ (incubating) 0.2.0
On behalf of the Teaclave community, I am happy to announce the second Apache Incubator release of Teaclave, 0.2.0. Teaclave is a universal secure computing platform, making computation on privacy-sensitive data safe and simple.
In 0.2.0, we focus on various components including built-in functions, SDKs in different languages, docker, command line interface, documents, etc.
Highlights
In version 0.2.0, we added more client SDKs in different languages; Rust, C, and even Swift. In Teaclave Meetup #2, we introduced the design of client SDKs. Basically, we are using JSON serialization/deserialization to make the interface simple and easy to work on.

0.2.0 Release Notes
Specifically, we have following updates:
Functions
- Add the builtin PCA (Principal Component Analysis) function
- Add the exposed password checking built-in function (#447)
SDK
- Add Rust client SDK (#455)
- Add C client SDK and examples (#470)
- Add Swift SDK (iOS framework)
- Change CMAC format from string to bytes array
Docker
- Add a
teaclave-file-servicecontainer to the docker compose file to help run the examples (#446) - Fix sim mode docker compose file (#462)
CLI
- [cli] Add the attest subcommand to display attestation report from the remote Teaclave service
Documents
- [docs] Add permalink for codebase's README (#428)
- [docs] Add document of Deploying Teaclave on Azure Confidential Computing Virtual Machines
Bug Fixes
- [binder] Add checks and test case for input/output buffer. (#423)
Misc
- Start to use GitHub Action (#473)
- Add GitHub issue templates (#476)
- Document polishing
Download
Teaclave 0.2.0 can be downloaded at the download page. Note that
it is essential to verify the integrity of the downloaded file using the
PGP signature (the .asc file) or a hash (the .sha256 file).
Documentation
If it is the first time to try Teaclave, we provide a simple but clear tutorial to guide you getting stated with Teaclave by invoking your first function in Teaclave.
Basically, you can build the Teaclave platform using docker with these commands:
$ cd incubator-teaclave
$ docker run --rm -v $(pwd):/teaclave -w /teaclave \
-it teaclave/teaclave-build-ubuntu-1804-sgx-2.9.1:latest \
bash -c ". /root/.cargo/env && \
. /opt/sgxsdk/environment && \
mkdir -p build && cd build && \
cmake -DTEST_MODE=ON .. && \
make"
Launch all services with docker-compose using simulation mode:
$ (cd docker && docker-compose -f docker-compose-ubuntu-1804-sgx-sim-mode.yml up --build)
And invoke function with a Python client:
$ cd examples/python
$ PYTHONPATH=../../sdk/python python3 builtin_echo.py 'Hello, Teaclave!'
[+] registering user
[+] login
[+] registering function
[+] creating task
[+] approving task
[+] invoking task
[+] getting result
[+] done
[+] function return: b'Hello, Teaclave!'
If you want to understand the internals of Teaclave, we provide several documents about the design of Teaclave. Also, we extensively document our codebase in each sub directories. At last, API references are automatically generated and uploaded to our homepage.